
Cobus Pool has been active in the control, automation and
industrial security arena for the past 20 years. He has exten-
sive experience in the power generation, petrochemical and
oil and gas environments. He is a registered professional
engineer and has received cyber security training from,
among others, the United States Department Of Homeland
Security. He specialises in security audits for control and electrical systems
and assists companies in establishing security structures.
Enquiries: Tel. 017 620 9725 or email
cobus.pool@proconics.co.zaCONTROL SYSTEMS + AUTOMATION
traffic analysis) systems provide some possibility of locating and
correcting these types of attacks. Prevention is unlikely.
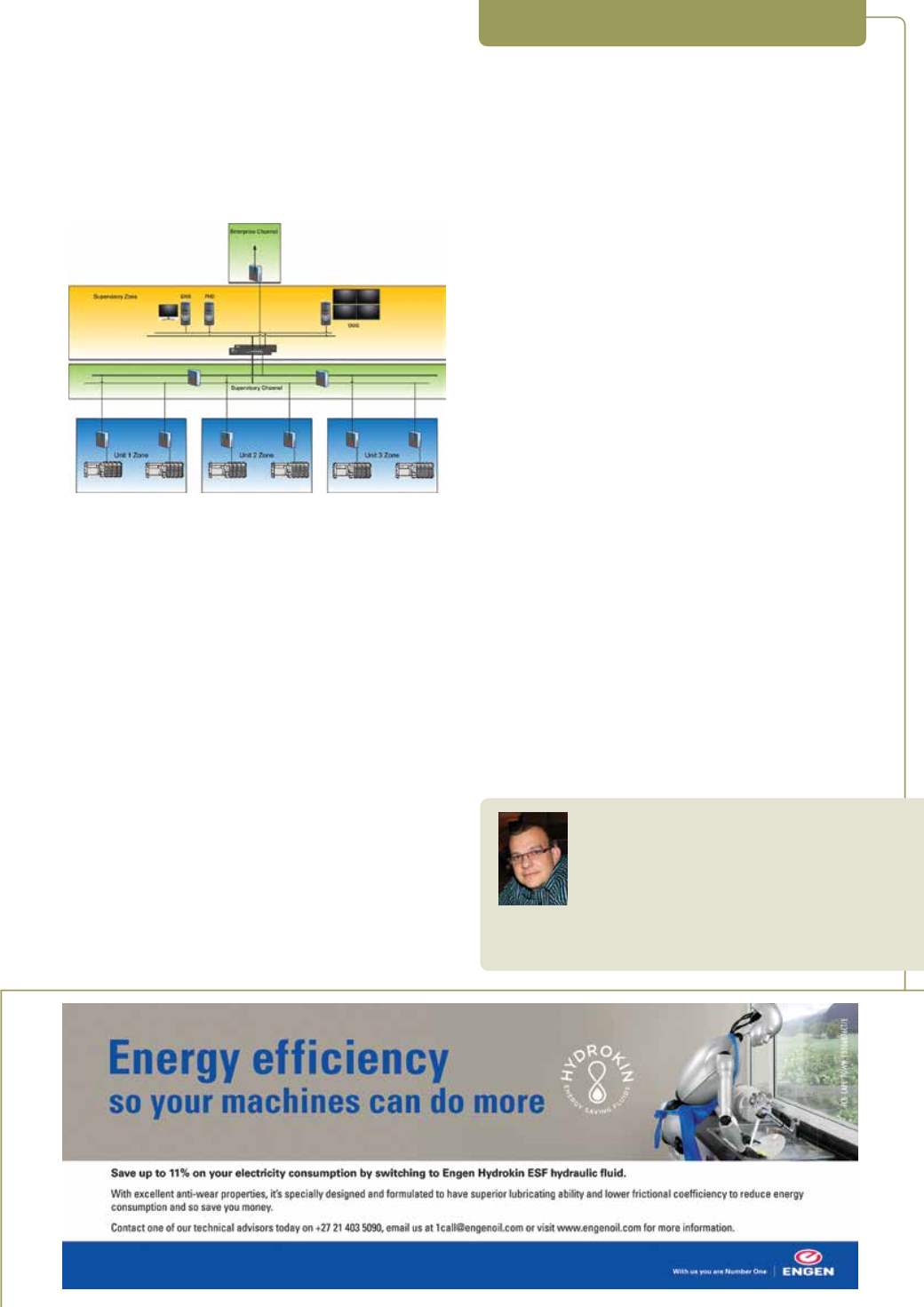
Figure 8: Practical implementation of DiD segmentation (copyright –
company represented by the author).
Conclusion
The threat against ICS systems is not decreasing and protection, good
practices and monitoring are becoming ever more important. While
measures are being put in place by government to ensure better protec-
tion through a legislative framework, we are still far behind and much
still needs to be done especially in the protection of production systems.
The onus will rest on the system owners to ensure that until this is in
place, protection of critical control and safety systems is catered for.
Cyber crime is a global problem and South Africa is not exempt. The
first step is to create awareness that there is a problem. DiD will not
protect against all threats, and especially not against the insider threat,
but together with good intrusionmonitoring and vulnerability scanning
and patching your systems will be much better protected.
Acknowledgement
The author presented this topic at the Safety Control Systems &
Hazardous Areas Conference 2015, held in Johannesburg, organised
by IDC Technologies.
References
[1] Turk RJ. 2005. Cyber Incidents Involving Control Systems. Idaho
National Laboratories, INL/EXT-05-00671.
[2] ICS-CERT Monitor. September 2014 – February 2015. US DHS
ICS-CERT.
[3] Skade T. 2013. Beware of the Trojan Horse on your stoep. http://
www.destinyconnect.com/2013/11/21/beware-of-the-trojan-horse-on-your-stoep/, from a report of the FBI.
[4] Cyber crime: South Africa thirdmost hard hit country. 2013. http://
www.flarenetwork.org/learn/africa/article/cybercrime_south_af-
rica_third_most_hard_hit_country.htm, from Symantec report.
[5] Draft Cyber Security Policy of South Africa. 2010, Government
Gazette no: 32963 Vol. 536.
[6] Strydom J. 2013. Meet the National Cyber Security Advisory
Council.
http://www.bandwidthblog.com/2013/10/16/meet-the-national-cyber-security-advisory-council/.
[7] Byres E and Cusimano J. 2012. 7 Steps to ICS and SCADA Security.
Version 1, Tofino Security | exida Consulting LLC.
[8] Recommended Practice: Improving Industrial Control Systems
Cyber Security with Defence in-depth Strategies. 2009.,DHS,
National Cyber Security Division.
[9] CSET 4.1Usermanual. 2012. USDepartment of Homeland Security.
[10]Control systems are a target. 2013. SANS – Securing the human.
www.sans.org/ics[11]What you should know about SHODAN and SCADA. 2010. http://
www.digitalbond.com/blog/2010/11/02/what-you-should-know-about-shodan-and-scada/
[12]Weiss J. An ICS vulnerability beyond Stuxnet. January 2014.
Control Global.
http://www.controlglobal.com/blogs/unfettered/an-ics-cyber-vulnerability-beyond-stuxnet/
[13]S4X14 conference. 2014. Digital Bond,
http://www.digitalbond.
com/page/2/

















